Body
There are numerous security vulnerabilities in the SSL/TLS protocols prior to TLS 1.2 and we need to ensure that our systems are only running the latest versions of these essential pieces of security software. To make sure your application is configured to require these latest versions, use the following procedure. In order to support TLS 1.2 or higher, your Linux system must have a minimum version of RHEL7: OpenSSL 1.0.2k or RHEL6: Openssl 1.0.1e. Also, you must be running Apache version 2.2.23 or higher, older versions of Apache and OpenSSL will not support this version of the protocol.
Process
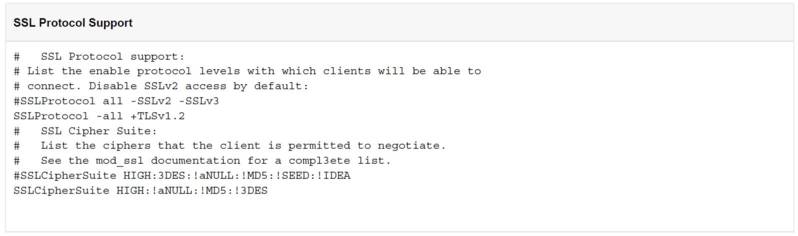
Use a text editor to change the following lines in the SSL configuration for the Apache webserver, the path should be /etc/httpd/conf.d/ssl.conf
- Comment out SSLProtocol all -SSLv2 -SSlv3 by adding a # in front of it.
- Add the line SSLProtocol -all +TLSv1.2
- Go further down the documents to the SSL Cipher Suite
- Comment out SSLCipherSuite HIGH:MEDIUM:!aNULL:!MD5:!SEED:!IDEA by adding a # in front of it.
- Add SSLCipherSuite HIGH:!aNULL:!MD5:!3DES under the commented out line
- Restart the httpd service with sudo service httpd restart
Troubleshooting
This could affect connectivity with your web application and some older browsers that don't support this version of TLS. Try troubleshooting with a known good client, to see if you can replicate the issue. If you have totally broken access to your application, please open a ticket with ITAC and we can help track down the possible cause of the issue.